[Most Asked : ML System Design Case Studies #23] What Happens When You Click Buy Now using Stripe : How it Actually Works
Uncovering all the engineering insights and technical details..
Table of Contents
User Transaction Flow
Technical Stack Deep Dive
Understanding the Fraud Detection Problem
Evolution from XGBoost to Deep Neural Networks
The Neural Network Architecture Revolution
Feature Engineering at Scale
Engineering Implementation Details
Engineering Insights & Conclusions
TL;DR
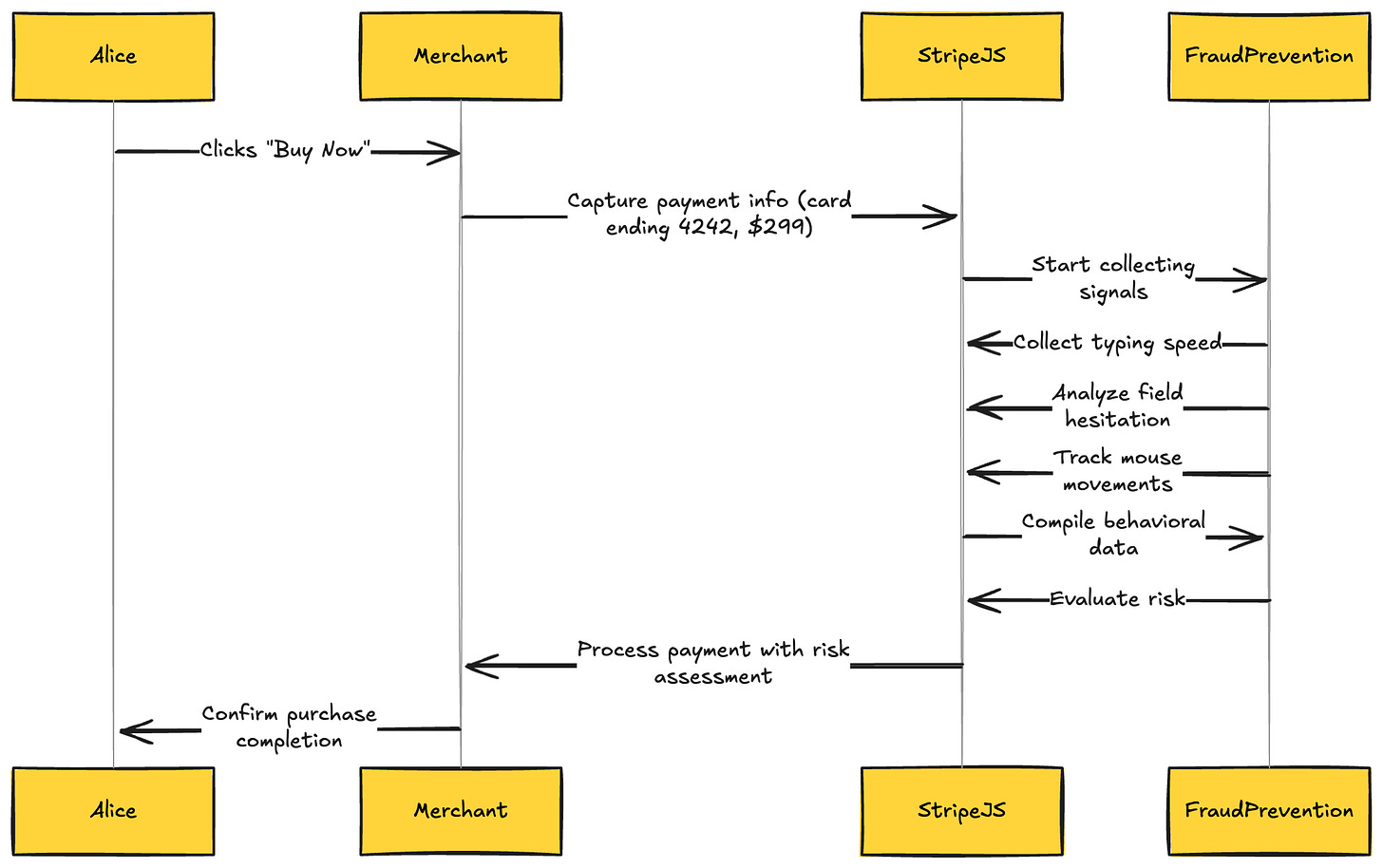
Let me start with what matters most - the split-second decision that happens when a customer clicks "Buy Now" on any website using Stripe. In less than 100 milliseconds, Stripe Radar analyzes over 1,000 characteristics of the transaction, makes a fraud determination, and either approves, blocks, or flags the payment for additional verification.
The Complete Transaction Flow
┌─────────────────────────────────────────────────────────────┐
│ USER TRANSACTION FLOW │
├─────────────────────────────────────────────────────────────┤
│ │
│ 1. CHECKOUT INITIATION │
│ ┌──────────────┐ │
│ │ User: Alice │ → Clicks "Buy Now" ($299 headphones) │
│ │ Card: •••4242│ → Payment form submitted │
│ └──────────────┘ │
│ ↓ │
│ │
│ 2. PAYMENT REQUEST (< 10ms) │
│ ┌──────────────────────────────────┐ │
│ │ • Card details encrypted │ │
│ │ • IP: 192.168.1.1 captured │ │
│ │ • Device fingerprint generated │ │
│ │ • Browser: Chrome 115.0 │ │
│ └──────────────────────────────────┘ │
│ ↓ │
│ │
│ 3. FEATURE EXTRACTION (< 20ms) │
│ ┌──────────────────────────────────┐ │
│ │ • Card history: 5 prior purchases│ │
│ │ • IP reputation: Residential ISP │ │
│ │ • Velocity: 1st purchase today │ │
│ │ • Email: alice@company.com │ │
│ │ • 1,000+ features computed │ │
│ └──────────────────────────────────┘ │
│ ↓ │
│ │
│ 4. NEURAL NETWORK SCORING (< 40ms) │
│ ┌──────────────────────────────────┐ │
│ │ DNN Input: 1,000+ features │ │
│ │ ↓ │ │
│ │ Multi-branch processing │ │
│ │ ↓ │ │
│ │ Fraud probability: 0.003 (0.3%) │ │
│ │ ↓ │ │
│ │ Decision: APPROVE ✓ │ │
│ └──────────────────────────────────┘ │
│ ↓ │
│ │
│ 5. RISK RULES ENGINE (< 10ms) │
│ ┌──────────────────────────────────┐ │
│ │ Custom rules check: │ │
│ │ • Amount < $1000? ✓ │ │
│ │ • Country allowed? ✓ │ │
│ │ • Velocity limit OK? ✓ │ │
│ │ Final: PROCEED │ │
│ └──────────────────────────────────┘ │
│ ↓ │
│ │
│ 6. TRANSACTION RESULT │
│ ┌──────────────────────────────────┐ │
│ │ Status: APPROVED │ │
│ │ Charge ID: ch_3N8xY2... │ │
│ │ Risk Score: Low (0.3%) │ │
│ │ Processing time: 92ms │ │
│ │ [Continue to confirmation page] │ │
│ └──────────────────────────────────┘ │
│ │
│ Total Latency: < 100ms ⚡ │
└─────────────────────────────────────────────────────────────┘
Breaking Down Each Step
Step 1: Checkout Initiation The moment Alice clicks "Buy Now" on her favorite electronics store, the fraud prevention journey begins. Her payment information - card number ending in 4242, billing address, and the $299 transaction amount - is captured by Stripe's JavaScript library embedded in the merchant's checkout page. This library immediately starts collecting behavioral signals: how quickly she typed her card number (fraudsters often paste), whether she hesitated on certain fields, and mouse movement patterns that distinguish humans from bots. All of this happens invisibly, without adding friction to Alice's checkout experience.
Read Implemented LLMs System Design (recommended to complete previous parts) -
Understanding Transformers & Large Language Models: How They Actually Work - Part 1
Understanding Transformers & Large Language Models: How They Actually Work - Part 2
[LLM System Design #3] Large Language Models: Pre-Training LLMs: How They Actually Work - Part 3
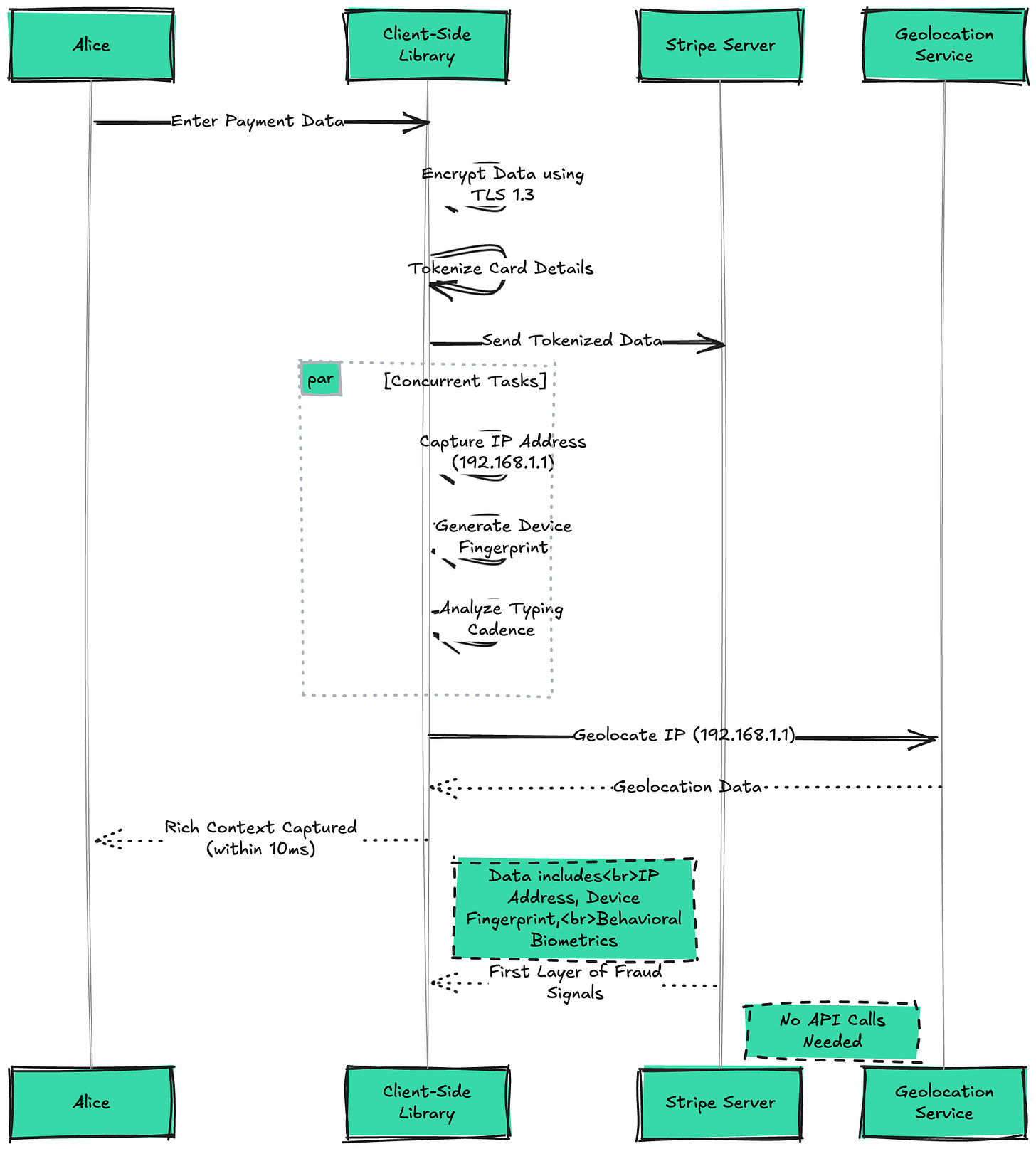
Step 2: Lightning-Fast Payment Request (< 10ms) The payment data is instantly encrypted using TLS 1.3 and tokenized, replacing sensitive card details with a secure token. Simultaneously, Stripe's client-side library captures critical context: Alice's IP address (192.168.1.1), which will be geolocated to check for impossible travel patterns; a device fingerprint combining browser version (Chrome 115.0), screen resolution, installed plugins, and timezone; and behavioral biometrics like typing cadence. This rich context, collected in under 10 milliseconds, provides the first layer of fraud signals without any API calls.
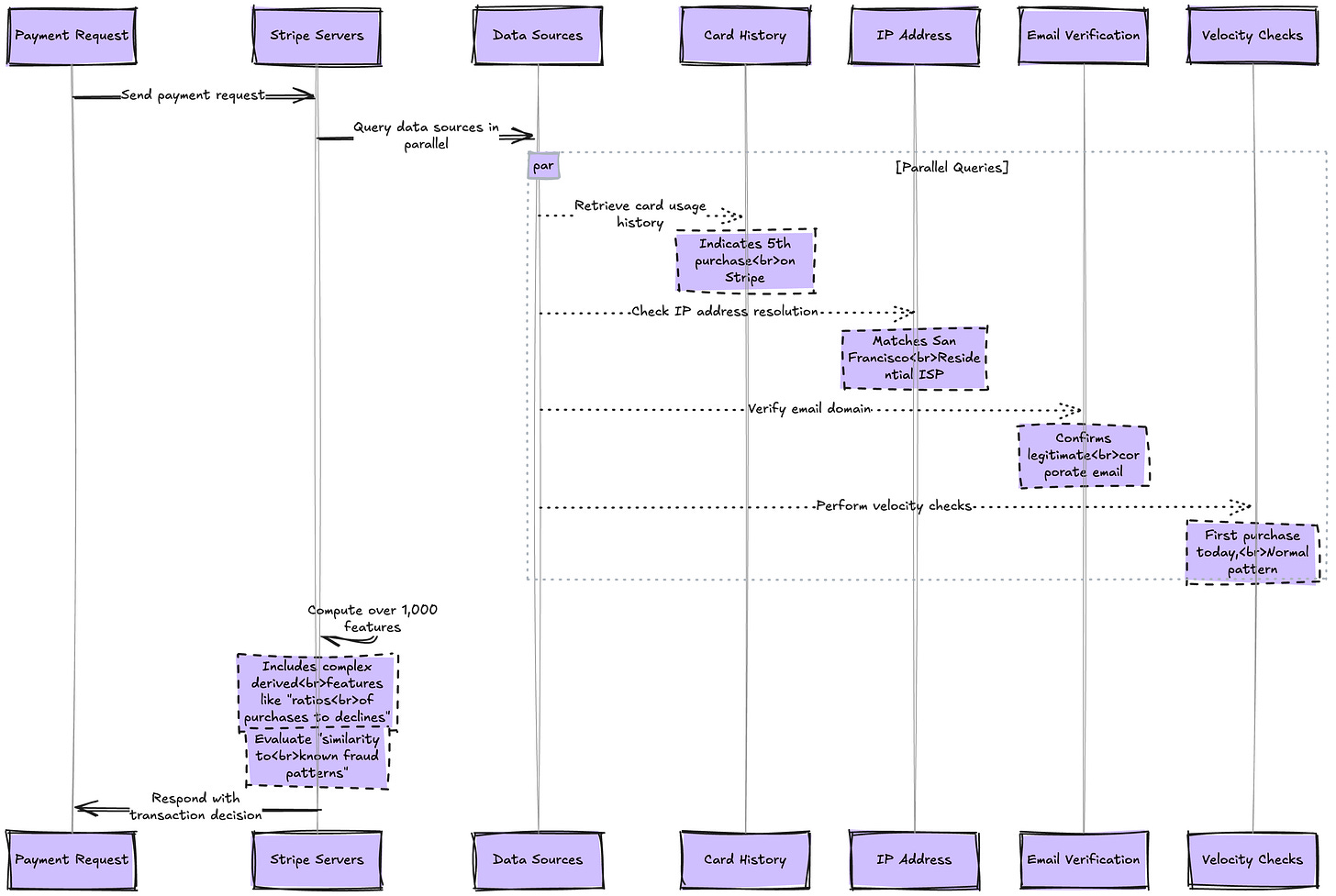
Step 3: Feature Extraction and Enrichment (< 20ms) As the payment request hits Stripe's servers, the real magic begins. Within 20 milliseconds, the system queries multiple data sources in parallel to build a complete picture of this transaction. The card history shows this is Alice's 5th purchase with this card on Stripe's network - a positive signal. The IP address resolves to a residential ISP in San Francisco, matching the billing address. Email domain verification confirms alice@company.com is a legitimate corporate email, not a throwaway address. Velocity checks show this is her first purchase today, well within normal patterns. Over 1,000 features are computed, including complex derived features like "ratio of purchases to declines in the last 30 days" and "similarity to known fraud patterns."
Step 4: Neural Network Scoring (< 40ms) The assembled feature vector feeds into Stripe's deep neural network - a sophisticated multi-branch architecture inspired by ResNeXt. The network processes features through multiple parallel branches, each specializing in different aspects: one branch focuses on card-specific patterns, another on merchant-specific signals, and others on velocity and behavioral features. These branches converge through attention mechanisms that dynamically weight their importance. For Alice's transaction, the network recognizes patterns of legitimate behavior: consistent purchase history, matching geographic signals, and normal transaction amounts for electronics. The model outputs a fraud probability of just 0.003 (0.3%) - well below the threshold for concern. The decision: APPROVE.
Step 5: Custom Rules Engine (< 10ms) Even with ML approval, the transaction passes through the merchant's custom rules. This electronics store has configured rules to flag transactions over $1,000 for manual review and block certain high-risk countries. Alice's $299 purchase from the US passes all rules. The velocity limiter confirms she hasn't exceeded the merchant's configured limit of 5 purchases per day. Some merchants add rules like "require 3D Secure for first-time customers" or "flag mismatched billing/shipping countries." This rules layer gives merchants control while benefiting from Stripe's network-wide fraud detection.
Step 6: Transaction Completion In just 92 milliseconds - faster than the blink of an eye - the entire fraud check completes. Alice sees "Payment Successful" and proceeds to the confirmation page. Behind the scenes, Stripe generates a unique charge ID (ch_3N8xY2...) and logs comprehensive data about the transaction and fraud decision. This data feeds back into the model training pipeline, continuously improving future predictions. If this had been a fraudulent transaction that somehow slipped through, the eventual chargeback would automatically label this transaction as fraud in the training data, helping the model learn from its mistakes.
The Technical Stack: Building Blocks of Real-Time Fraud Prevention
Now that we understand the user journey, let's dive deep into the sophisticated technical infrastructure that makes sub-100ms fraud detection possible while processing billions of transactions annually.
Below are the top 10 System Design Case studies for this week
Billions of Queries Daily : How Google Search Actually Works
100+ Million Requests per Second : How Amazon Shopping Cart Actually Works
Serving 132+ Million Users : Scaling for Global Transit Real Time Ride Sharing Market at Uber
3 Billion Daily Users : How Youtube Actually Scales
$100000 per BTC : How Bitcoin Actually Works
$320 Billion Crypto Transactions Volume: How Coinbase Actually Works
100K Events per Second : How Uber Real-Time Surge Pricing Actually Works
Processing 2 Billion Daily Queries : How Facebook Graph Search Actually Works
7 Trillion Messages Daily : Magic Behind LinkedIn Architecture and How It Actually Works
1 Billion Tweets Daily : Magic Behind Twitter Scaling and How It Actually Works
12 Million Daily Users: Inside Slack's Real-Time Messaging Magic and How it Actually Works
3 Billion Daily Users : How Youtube Actually Scales
1.5 Billion Swipes per Day : How Tinder Matching Actually Works
500+ Million Users Daily : How Instagram Stories Actually Work
2.9 Billion Daily Active Users : How Facebook News Feed Algorithm Actually Works
20 Billion Messages Daily: How Facebook Messenger Actually Works
8+ Billion Daily Views: How Facebook's Live Video Ranking Algorithm Works
How Discord's Real-Time Chat Scales to 200+ Million Users
80 Million Photos Daily : How Instagram Achieves Real Time Photo Sharing
Serving 1 Trillion Edges in Social Graph with 1ms Read Times : How Facebook TAO works
How Lyft Handles 2x Traffic Spikes during Peak Hours with Auto scaling Infrastructure..